How It Works
We Find the SaaS & Cloud Risks You Didn’t Know You Had — Then We Help You Kill Them

Waldo doesn’t just generate pretty dashboards. We go deep under the hood of your cloud and SaaS ecosystem to expose unauthorized apps, orphaned accounts, shadow tenants, and access risks hiding in plain sight. Then we give you the tools to take action — fast.
We integrate with your identity provider (IdP), scan your environment for shadow access, and deliver continuous visibility and governance.
In other words...
⚙️
Waldo finds it. ✔️
Waldo fixes it. ✔️
You move on. ✔️
⚙️
How Waldo Works
Step 1: Discover What's Really Out There
-
Automatically map all SaaS apps, cloud subscriptions, and unauthorized accounts in your environment
-
Identify untracked identities, rogue tools, and shadow IT in minutes
See our SaaS Discovery & Shadow IT pages
Step 2: Tie Every Identity to Real People (or Bots)
-
Connect the dots between accounts and actual users — or flag them if they’re orphaned, stale, or suspect
-
Spot identity risk and clean it up with smart, automated workflows
Explore our Offboarding tools:
Step 3: Automate Governance & Enforce Policy
-
Create access review policies that don’t depend on spreadsheets or overdue reminders
-
Surface high-risk access, enforce least privilege, and document everything
Learn more about SaaS Governance & Compliance

Step 4: Shrink Your Attack Surface, For Real
-
Kill zombie accounts
-
Eliminate risky access
-
Deactivate shadow SaaS
-
Build a cleaner, tighter, safer cloud stack
Waldo makes it painless — dare we say satisfying — to enforce security policies across your modern tech stack.


Automatic Discovery
Waldo Security analyzes only external emails that match specific patterns and requires only fragments of these emails to uncover unknown elements. With these email fragments, Waldo Security can detect new signups, new SaaS applications, and new accounts, and verify their compliance.
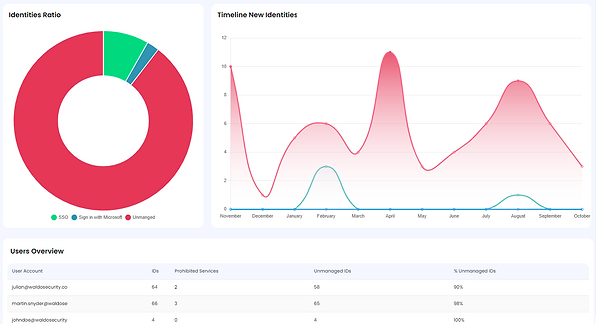
Get Complete Visibility
Gaining full visibility into your digital environment is essential for maintaining security and efficiency. This capability allows you to monitor all network activities, detect unauthorized access, and identify potential threats. With comprehensive insights, you can proactively manage risks and ensure regulatory compliance.
Waldo Security delivers this full visibility, offering complete oversight of your SaaS applications, accounts, and users.

Check non-compliant or non-authorized SaaS usage
Instantly determine whether specific accounts or SaaS applications comply with your internal policies or industry regulations. Receive alerts about new unauthorized and non-compliant accounts and SaaS within your environment.



Create Automated Workflows
Automated workflows can significantly enhance your efficiency by instantly notifying you about new SaaS applications or accounts, non-compliant issues, and unmanaged services.
These workflows can also automatically off-board non-compliant or unmanaged accounts and services, ensuring your environment remains secure and compliant without requiring constant manual intervention.
Get a Report
Waldo Security automatically generates executive reports on your current SaaS posture, new signups, and compliance violations, offering a clear overview of your environment's activity. These reports empower you to stay informed and make proactive decisions to maintain security and compliance.




